I hacked a .gov site
Table of Contents
Introduction
In June of 2025, a friend sent me a new .gov website that had recently been spun up less than 18 hours prior. I decided to look at the technologies the website was running and how information was displayed, and found an interesting URL parameter that looked something like this:
https://domain.gov/next/image?url=%2Fpath%2Fto%2Fimage.png&w=256&q=75
This potentially looked like a classic case of Server-Side Request Forgery!
Server Side Request Forgery
Server-Side Request Forgery (SSRF) is a vulnerability where an attacker can force a web server to make arbitrary requests to internal or external resources.
This can be utilized to access sensitive information stored on the web server, pivot into the server’s internal network, or turn the web server into a proxy for malicious domains.
Website Exploitation
Because the url= parameter to obtain images wasn’t properly sanitized, I was able to use the web server as a proxy to any domain I wanted.
Whenever I test for SSRF, I always point to ident.me since it’s simple and returns the web server’s true public IP address! Since this was a Cloudflare Worker, the address belonged to Cloudflare.
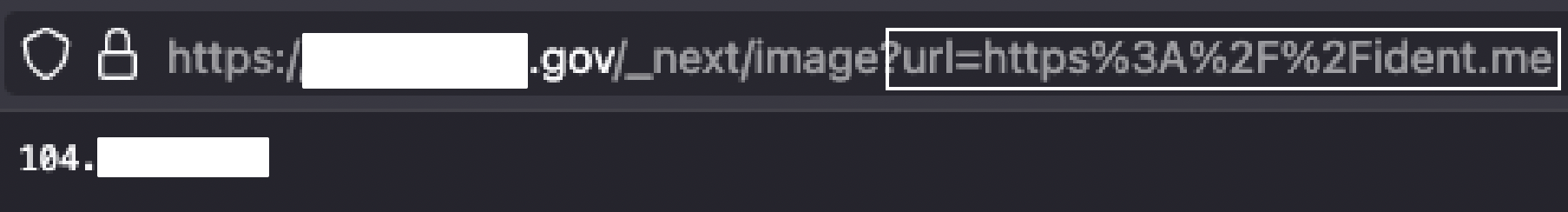
I could additionally navigate to and render websites with some limitations, but the proof of concept clearly worked:
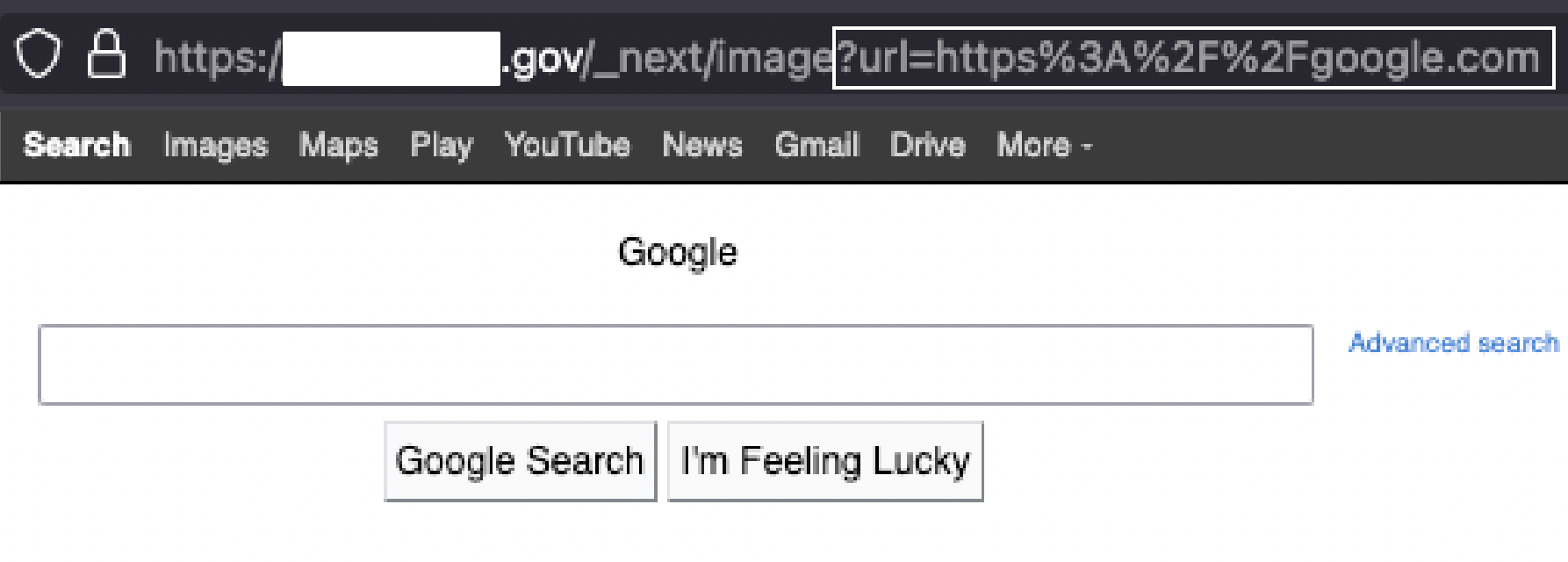
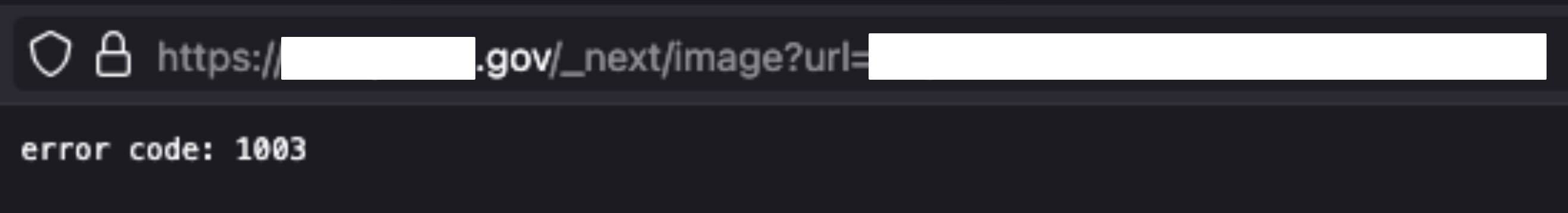
I was unable to pivot to an internal network because the website was hosted on Cloudflare, and requests to internal resources were rejected directly by them.
Ethical Disclosure Timeline
As soon as I could reasonably verify and replicate the vulnerability, I immediately tried to find an email associated with the website. I reached out to the IT manager and senior developer for the branch that launched the website, as well as the email listed in the domain’s WHOIS information.
The disclosure timeline was fairly simple. I discovered the vulnerability and sent a working proof-of-concept email to the recipients mentioned earlier, with a total of 31 minutes between discovery and notification.
I never received a response or acknowledgement that the email was received, but I did notice that the vulnerability was fixed at least five days later.
Conclusion
I wanted to wait at least six months before documenting the finding for a blog post and am being intentionally vague in case there are workarounds to the applied patch that I’m not aware of. Either way, this was a quick and fun little project with some real-world impact! :)